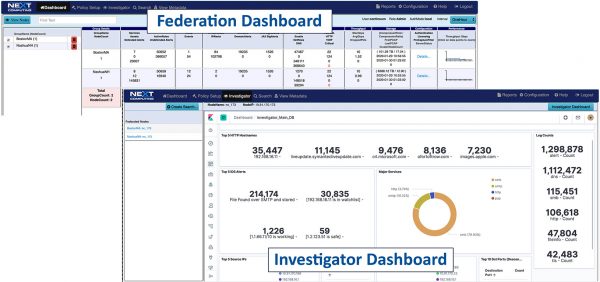
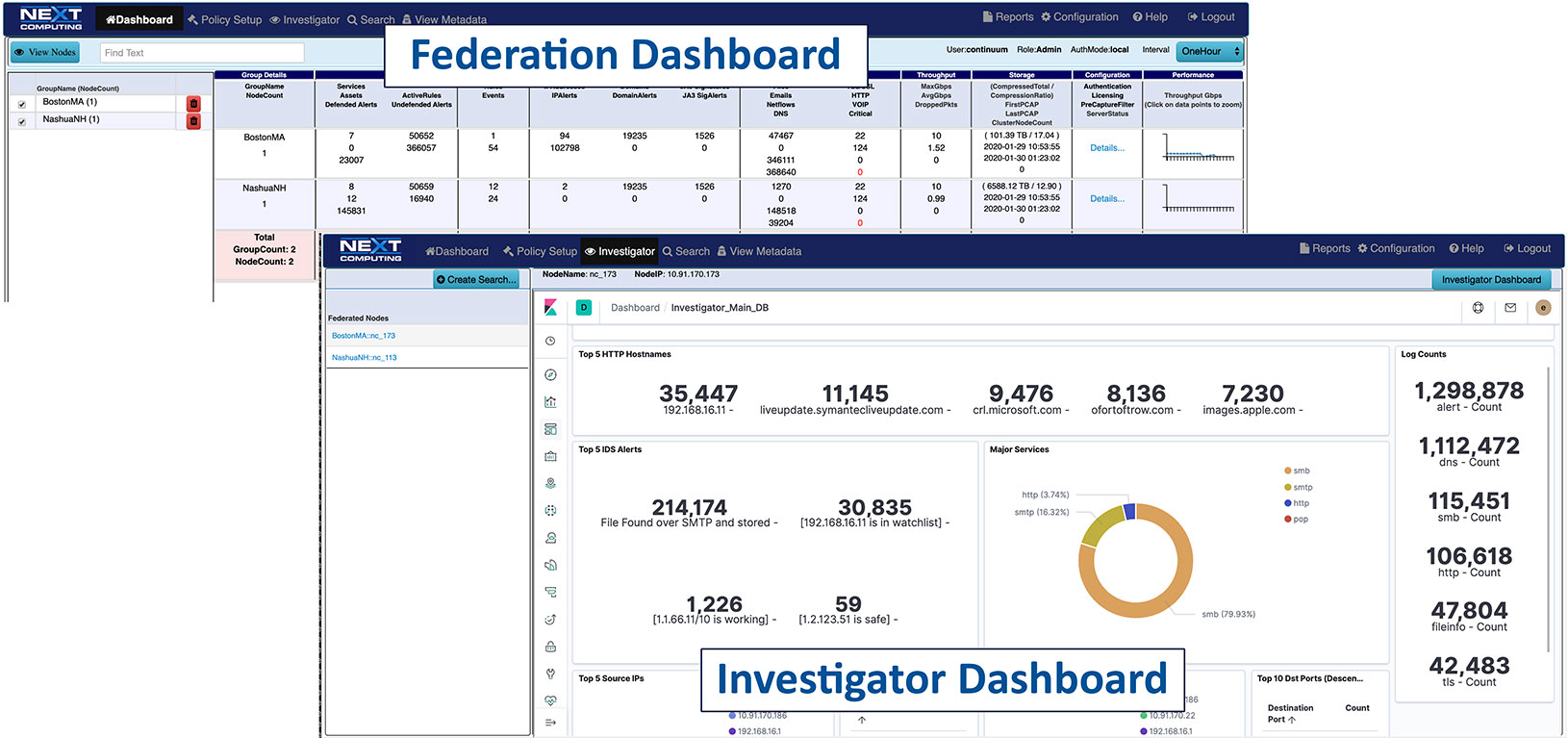
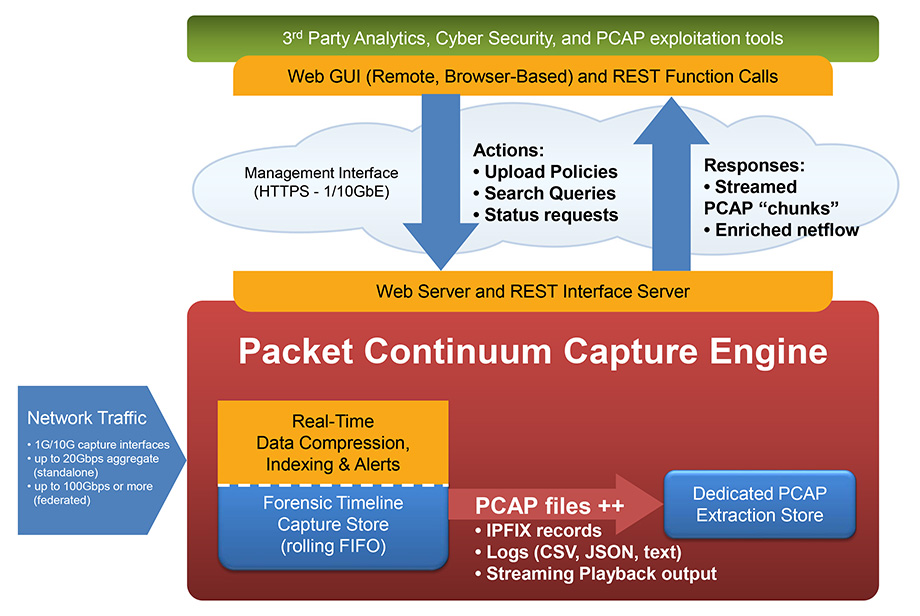
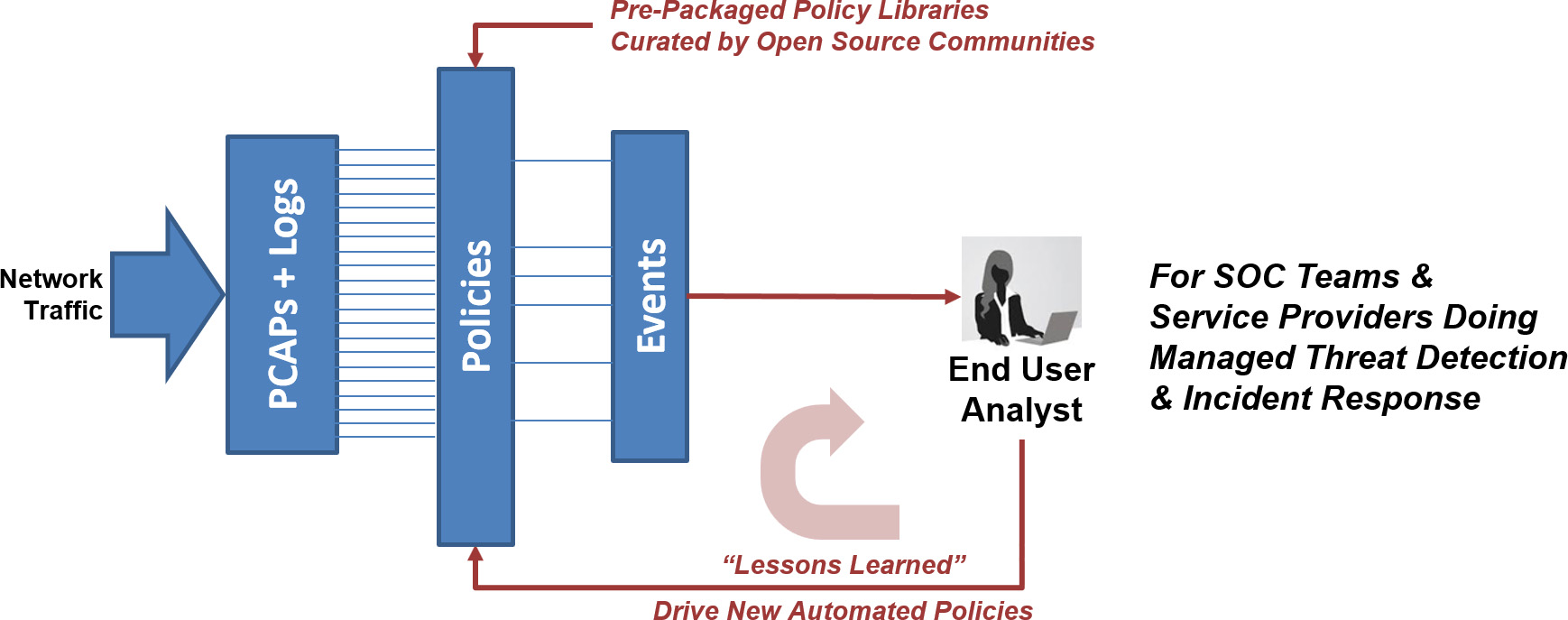
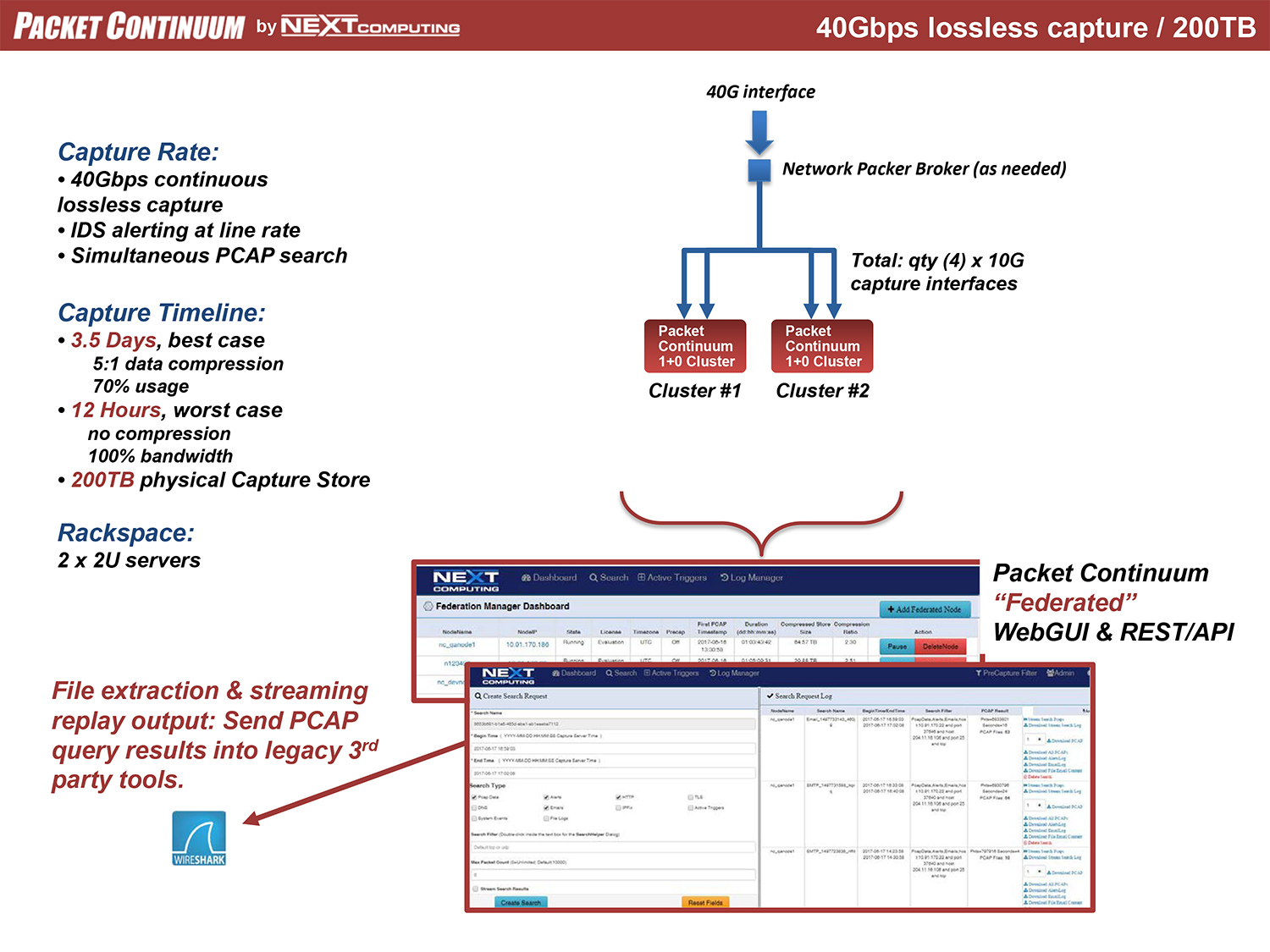
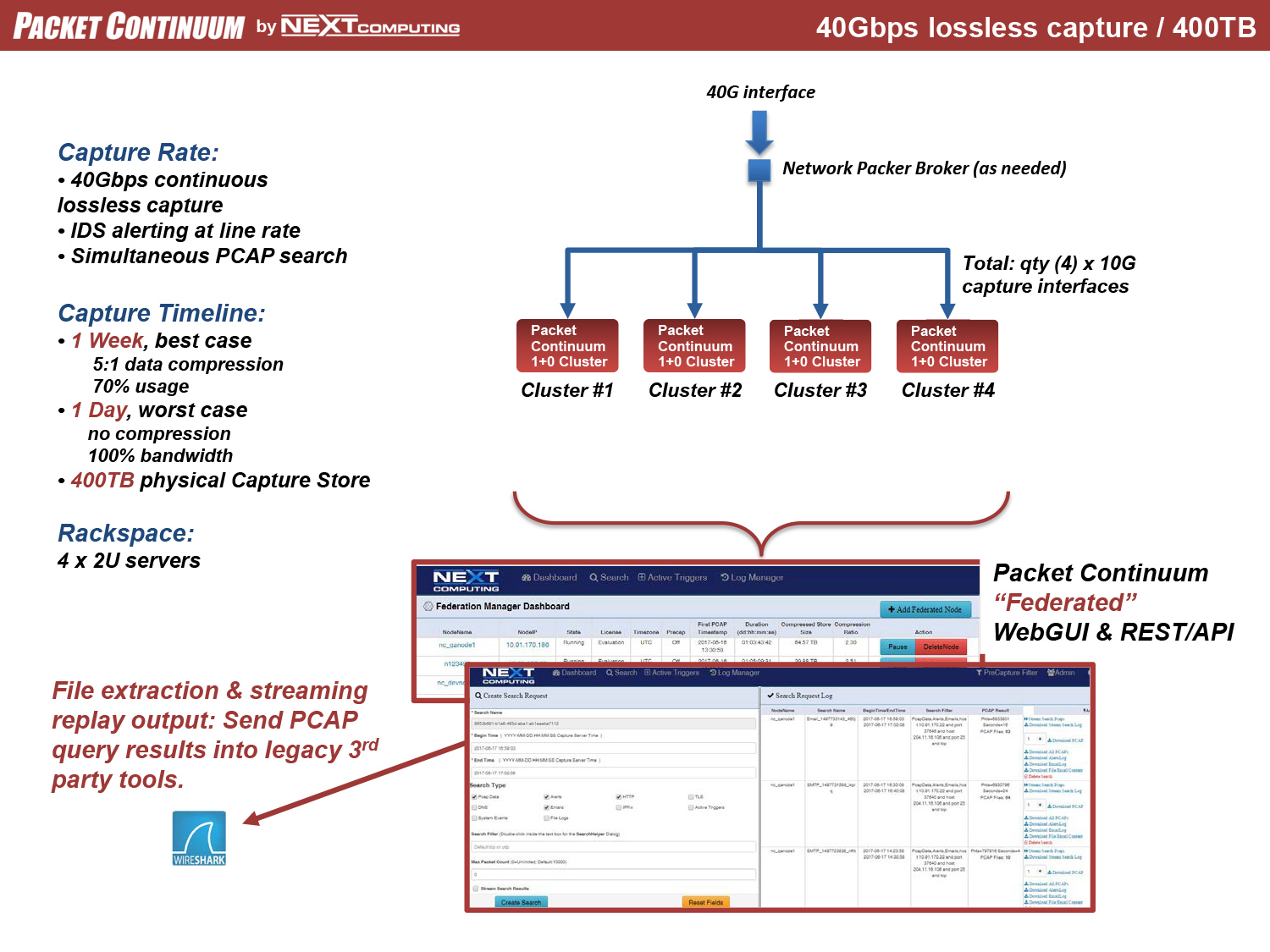
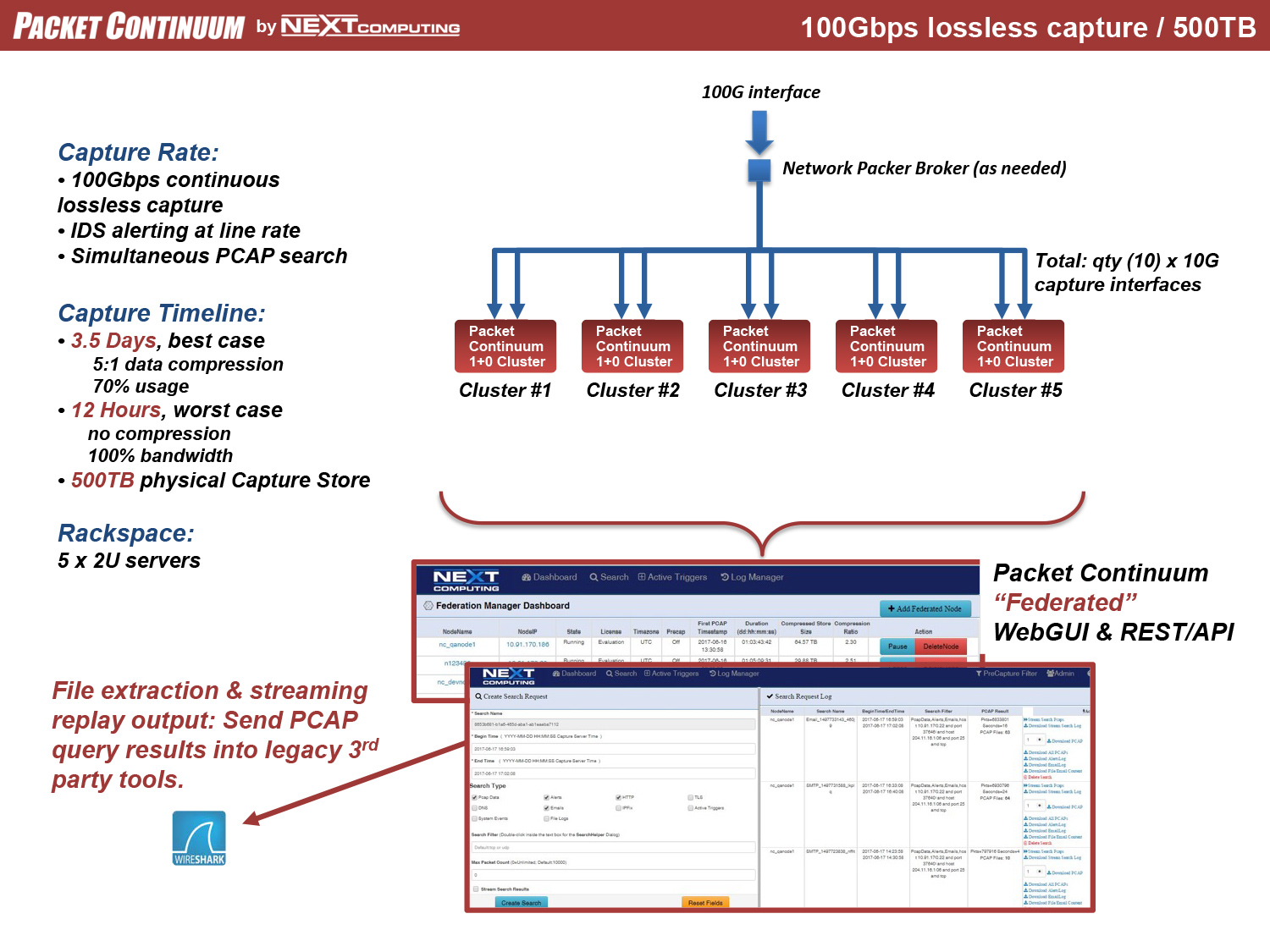
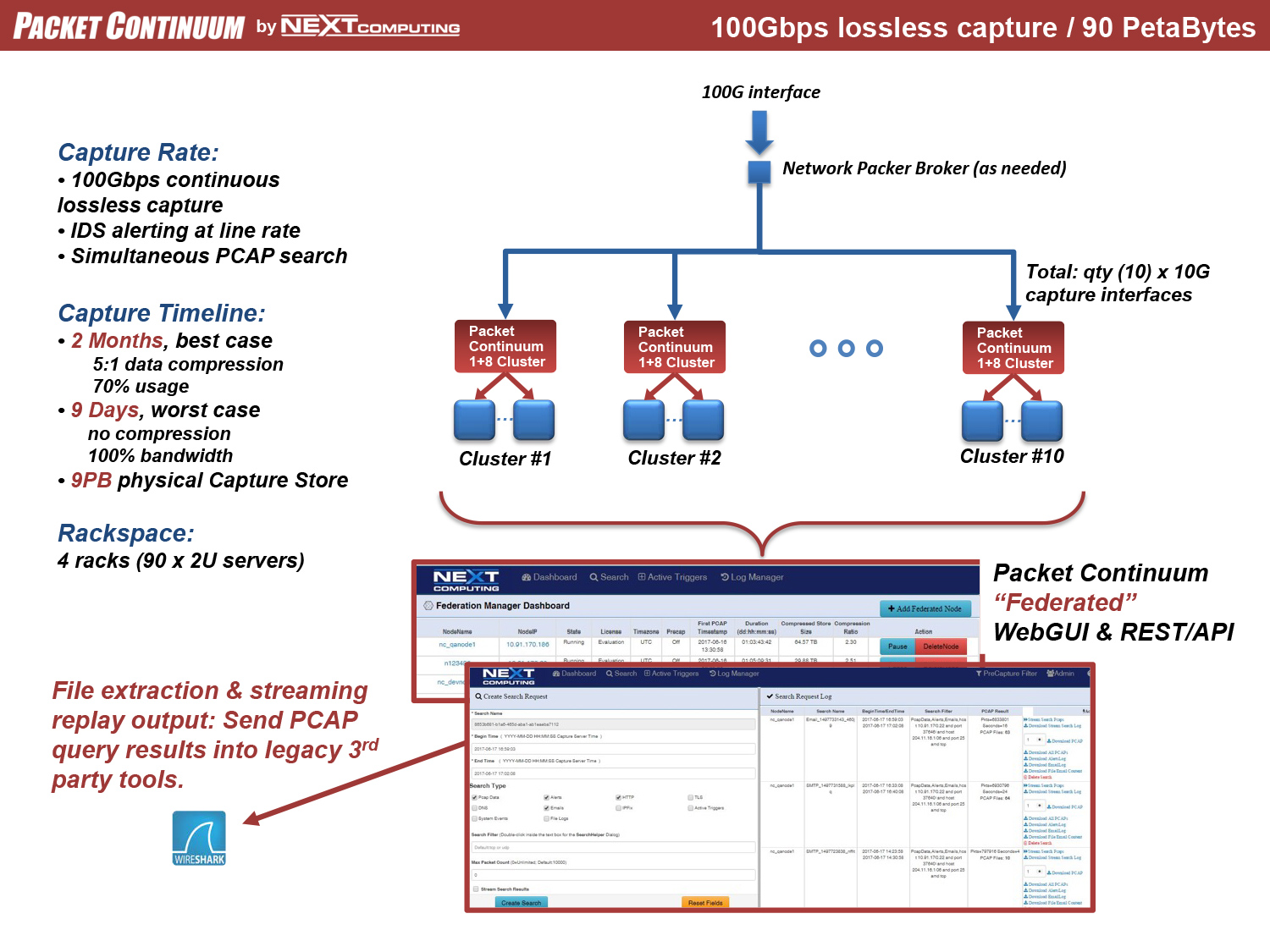
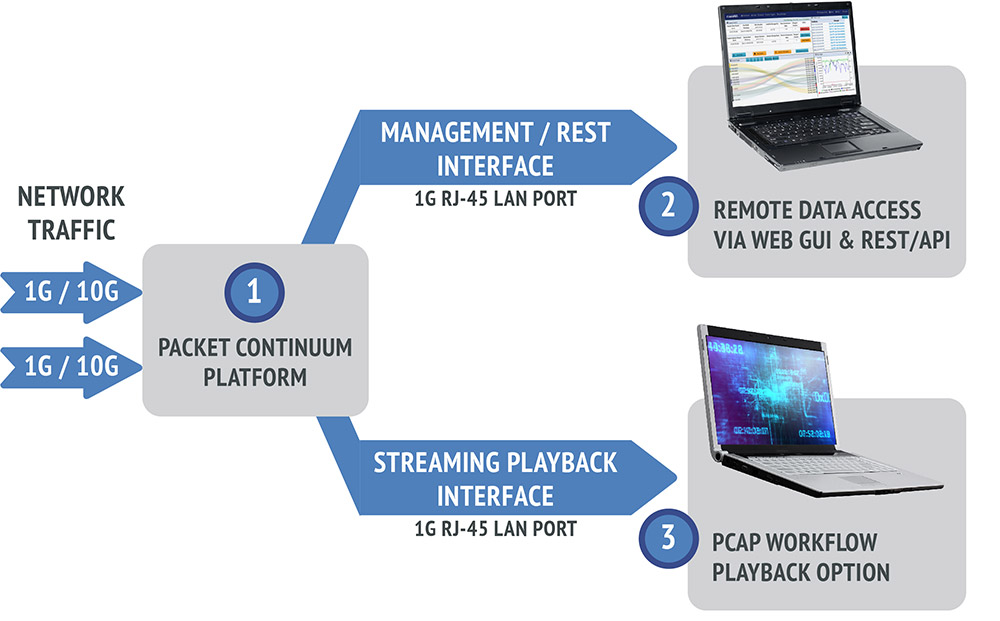
Real-time policy alerts, based on open-standards curated by open-source communities, allow analysts to rapidly triage network anomaly and security IoC events.
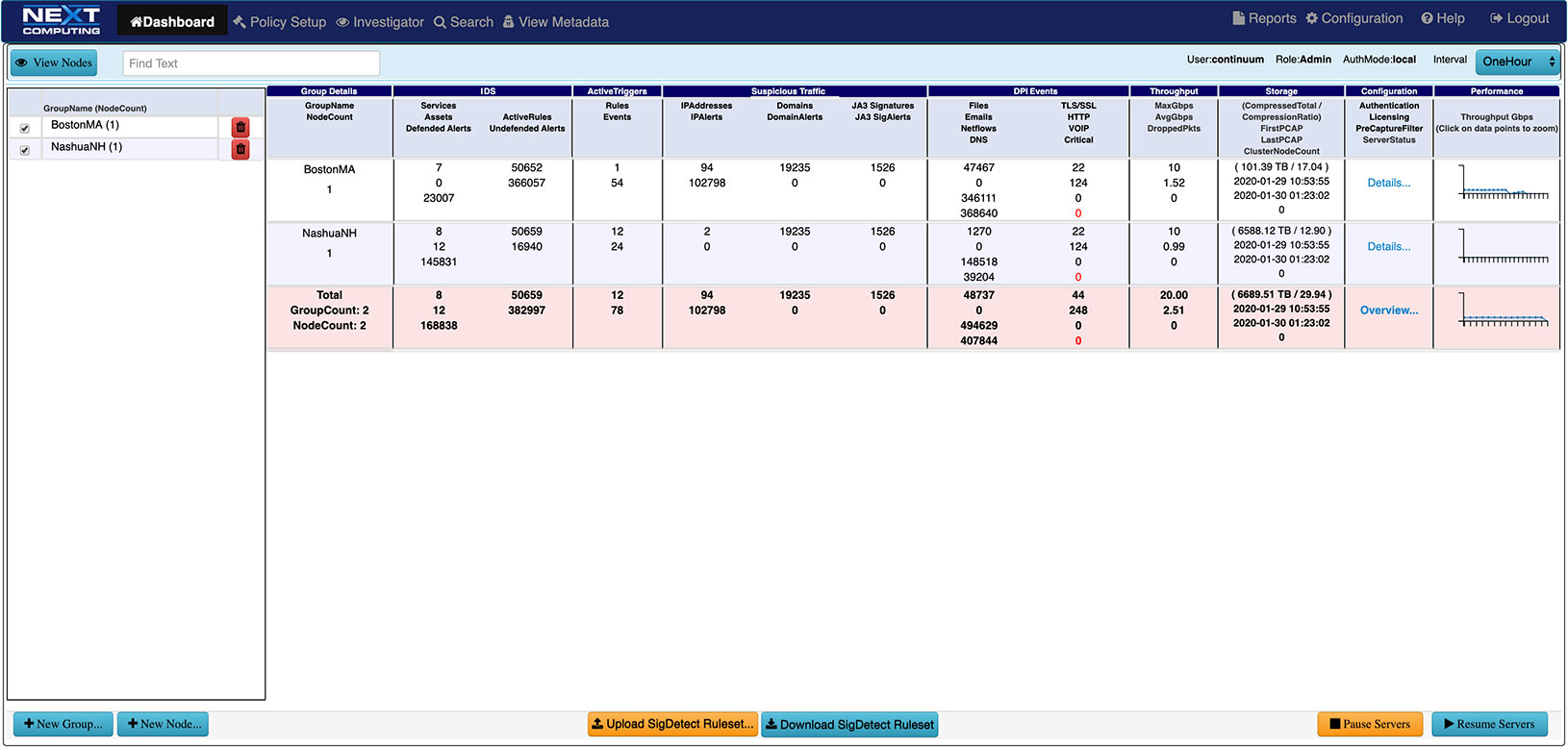
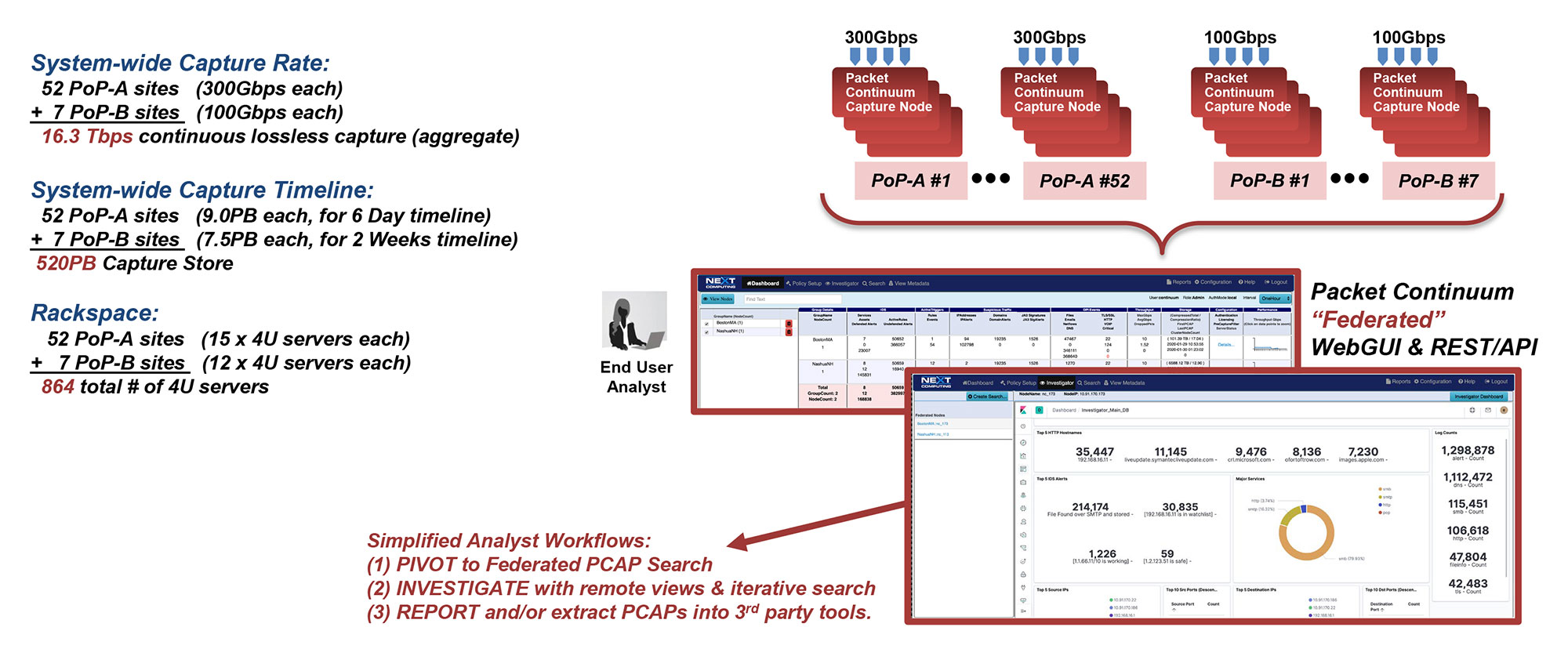
ANALYST OPERATIONS DASHBOARDS
- Prioritizes real-time Indicators of Compromise (IoC) & Incident Response actions
- Automated mapping of IoC events to adversary behavior in the Kill Chain
- One-click searches from the dashboard
- Live updates to the Capture Data Graph, and Critical Alerts List

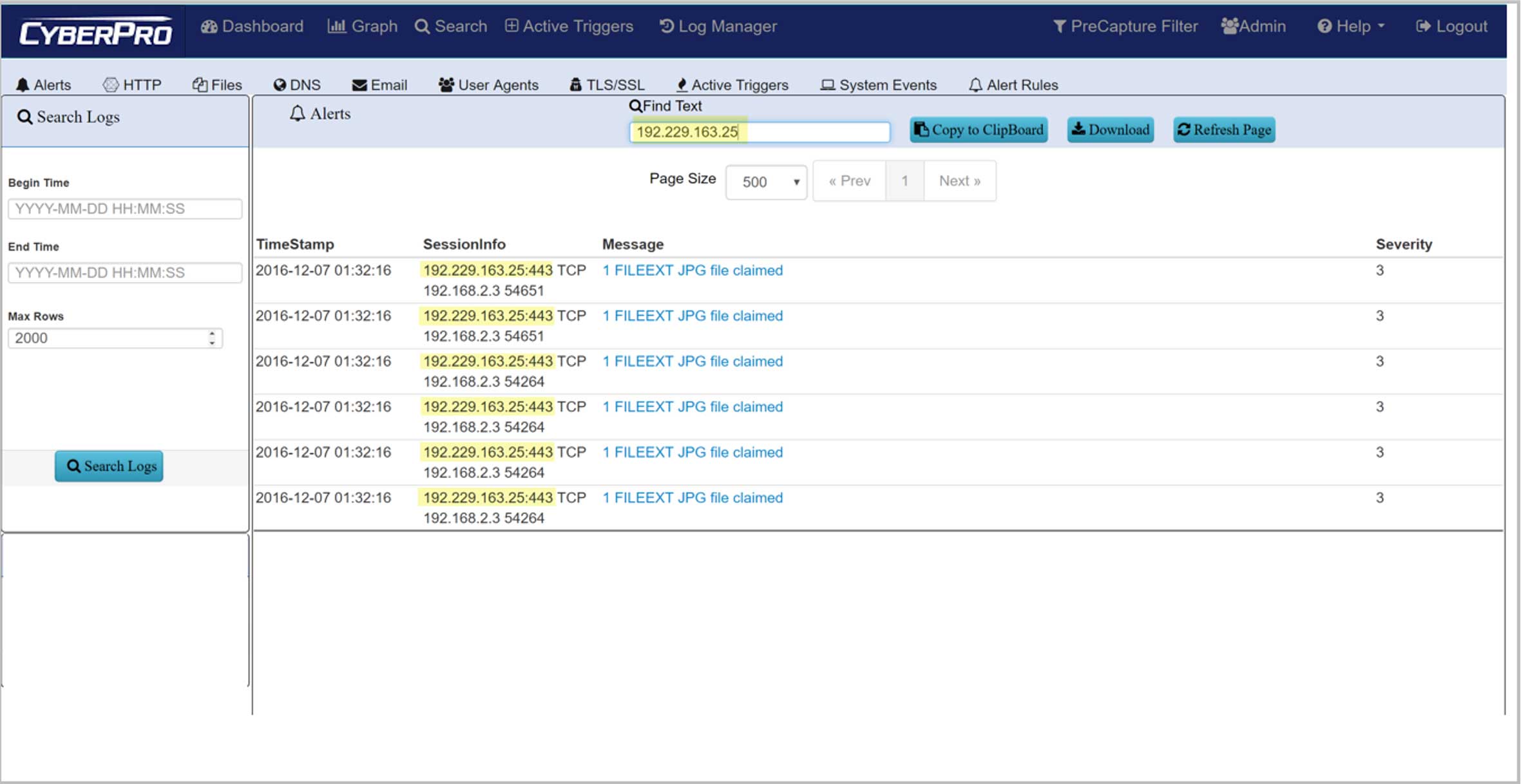
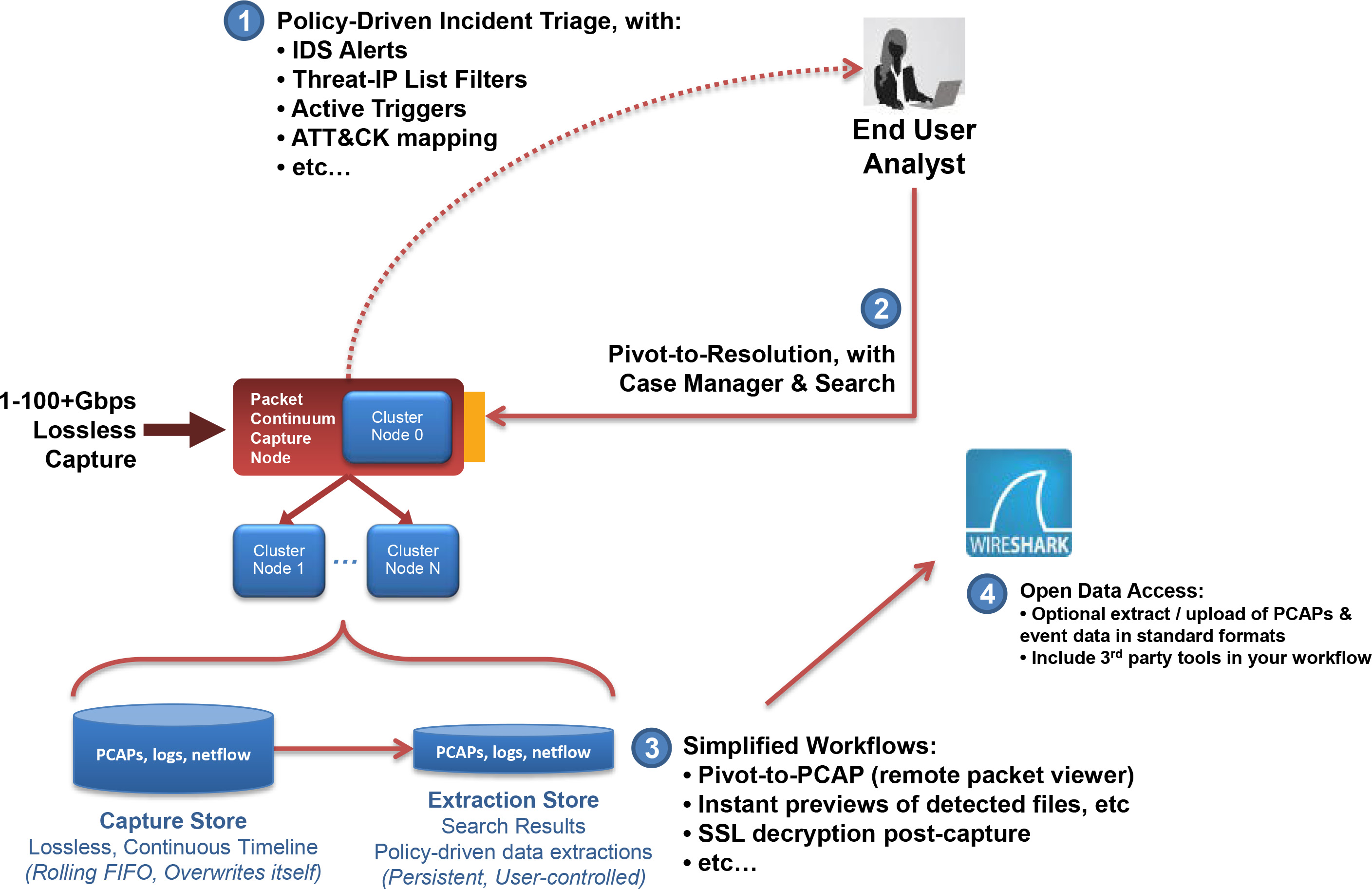
POLICY ALERTS DRIVE INCIDENT RESPONSE
- Start with red-flag behavior, like Exfiltration or suspect C&C activity
- One-click search to show IoCs for each step in the Kill Chain
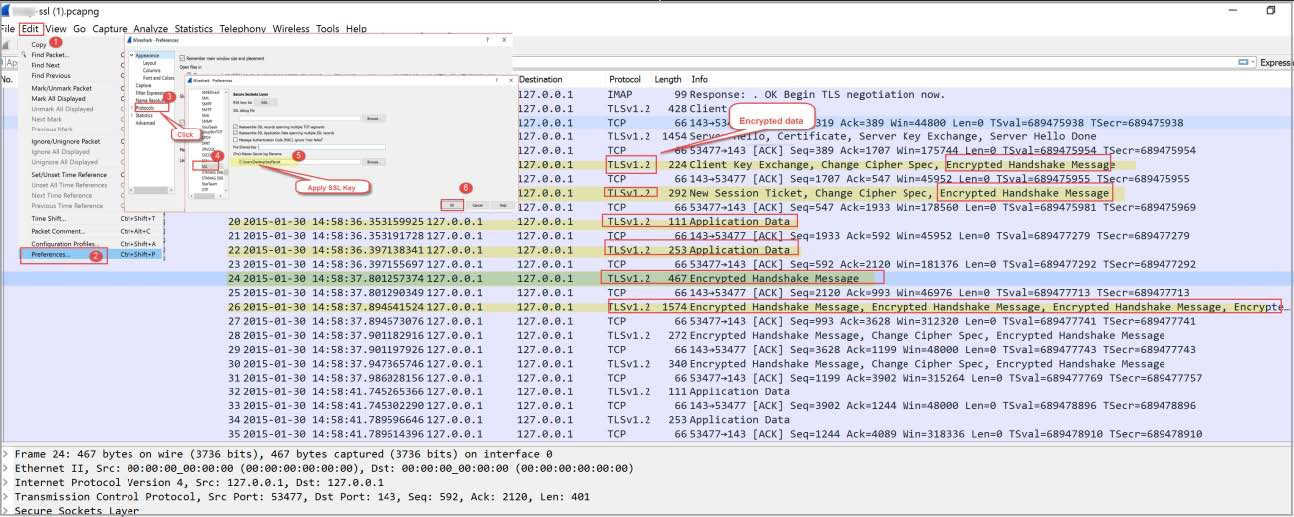
- Then click thru for all correlated PCAP data

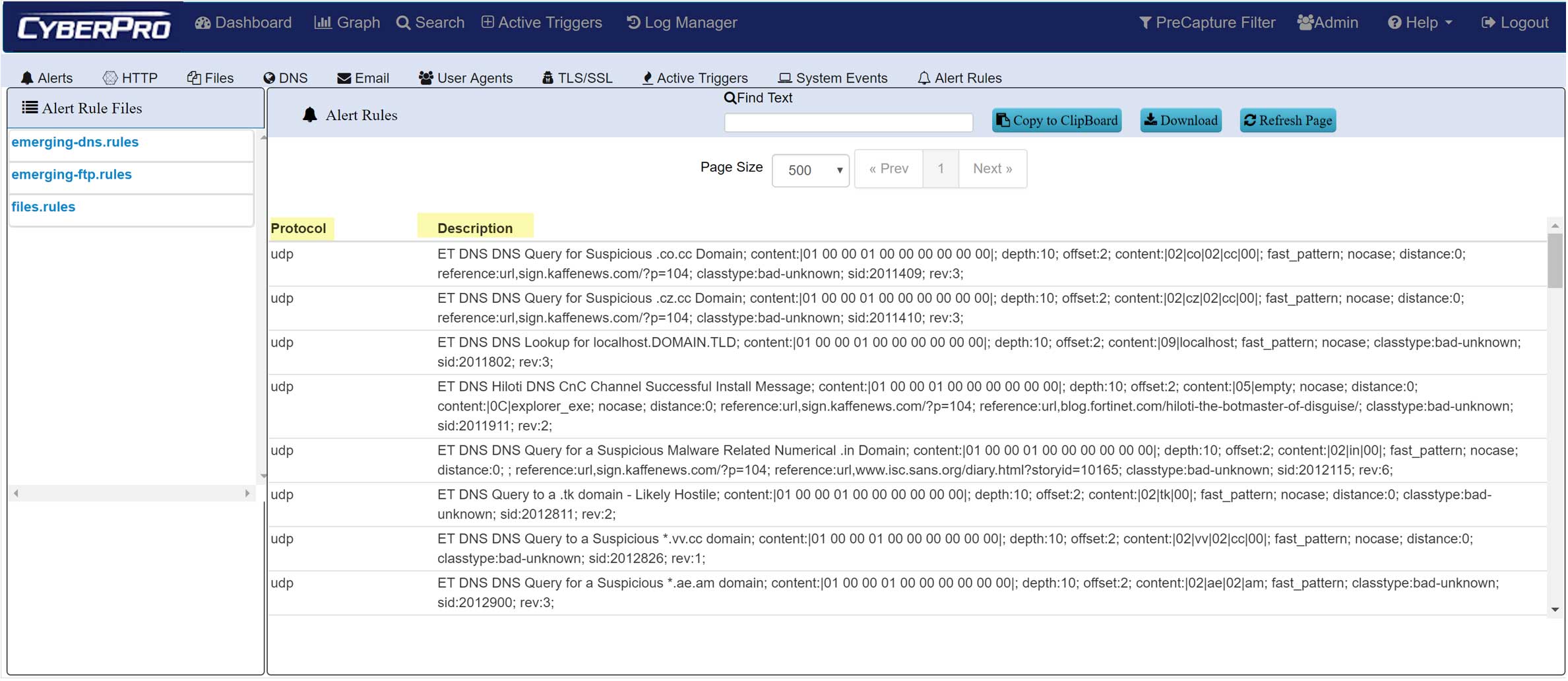
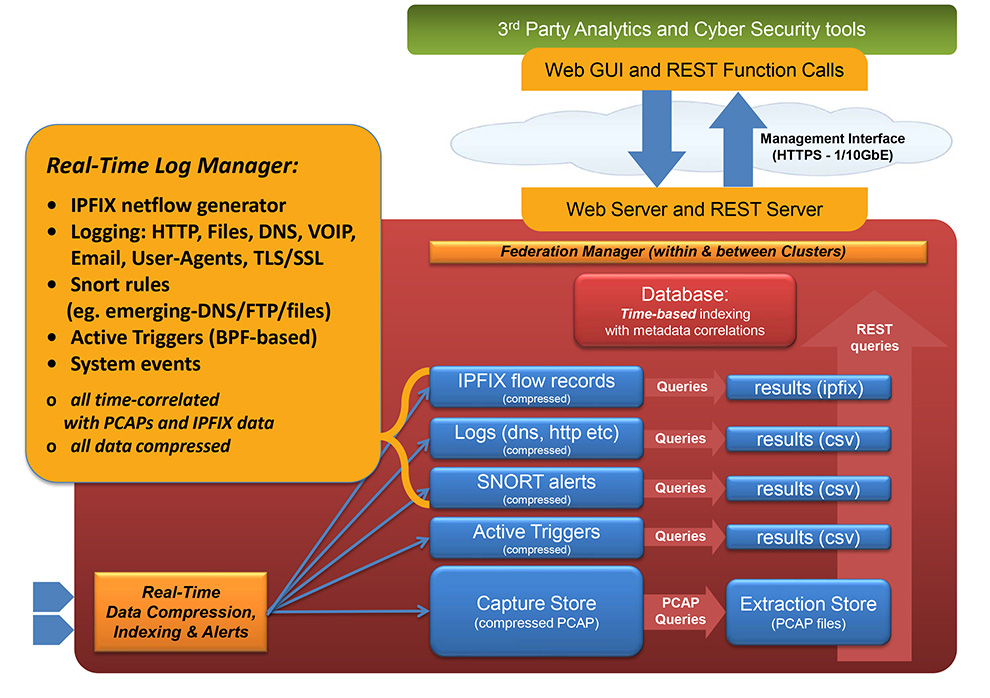
THREAT HUNTING – IOC POLICIES
- SNORT/SURICATA Rule Sets
- Threat IPs and Suspicious Traffic alerts
- Defended Assets & Services
- Active Triggers (BPF-based)

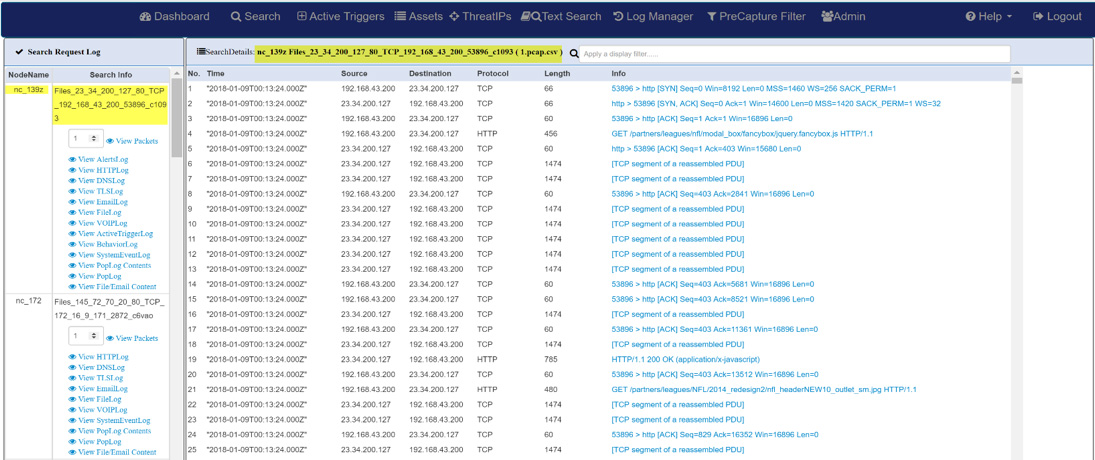
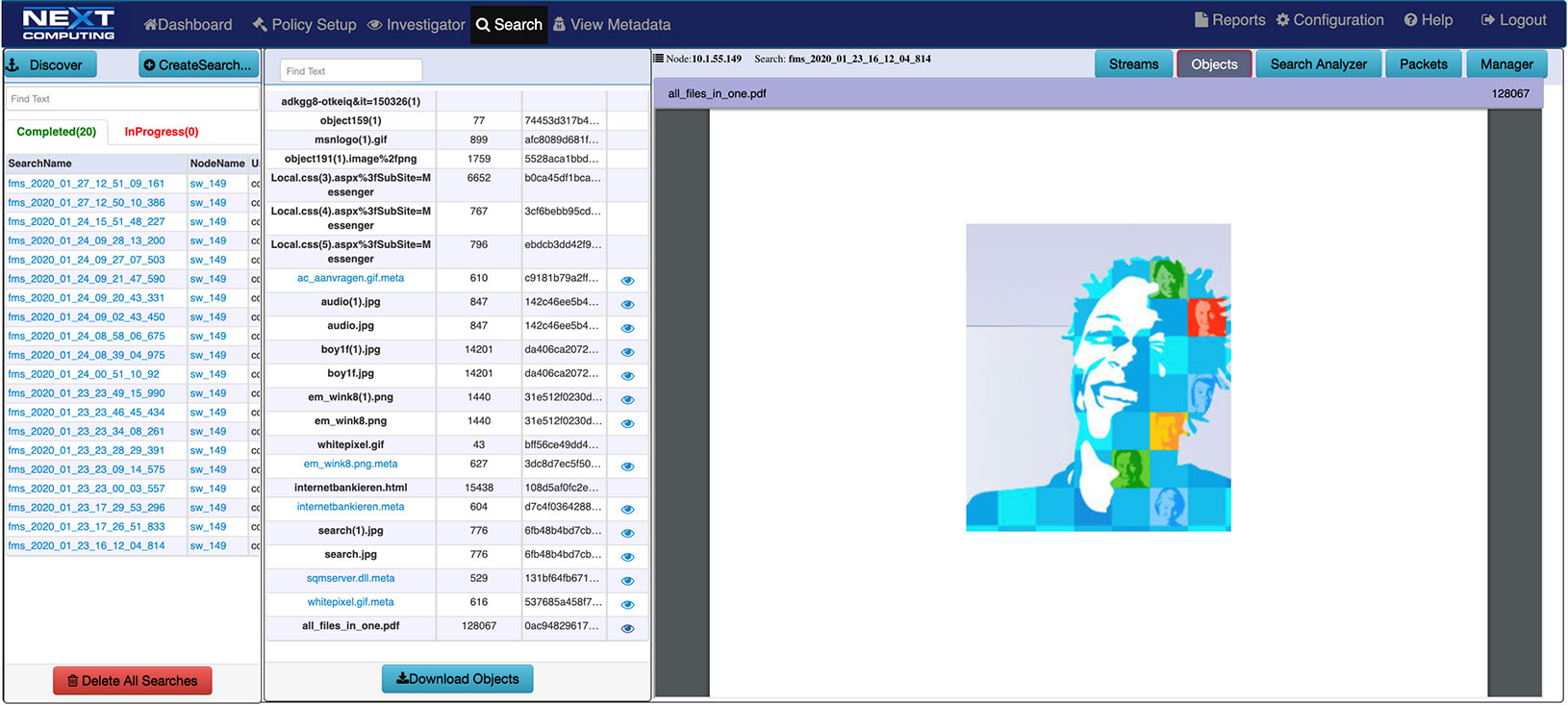
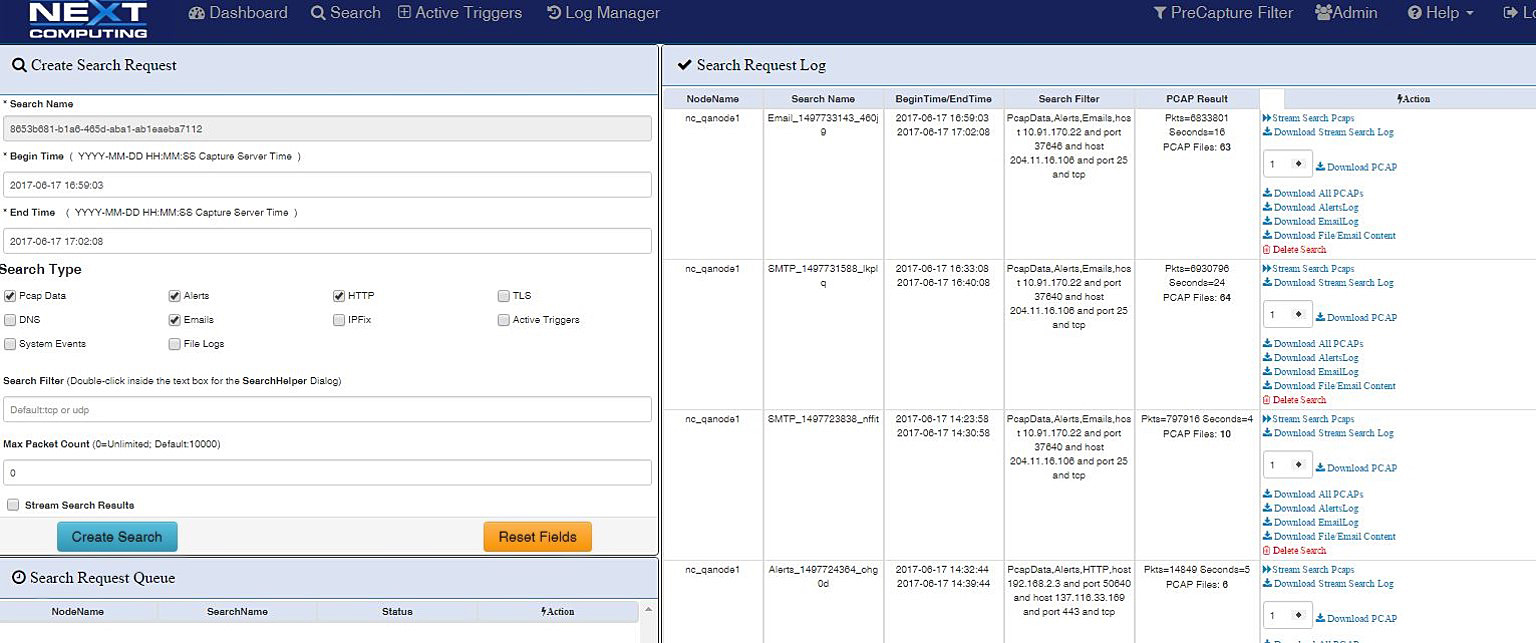
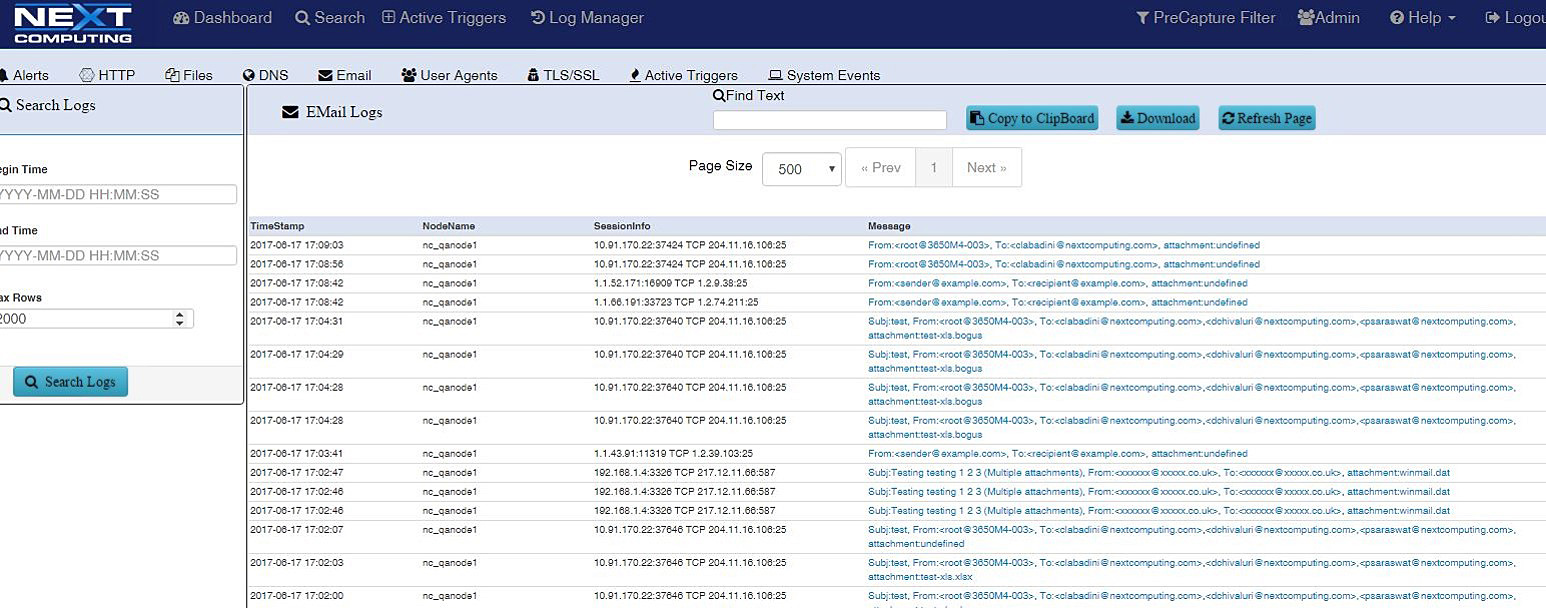
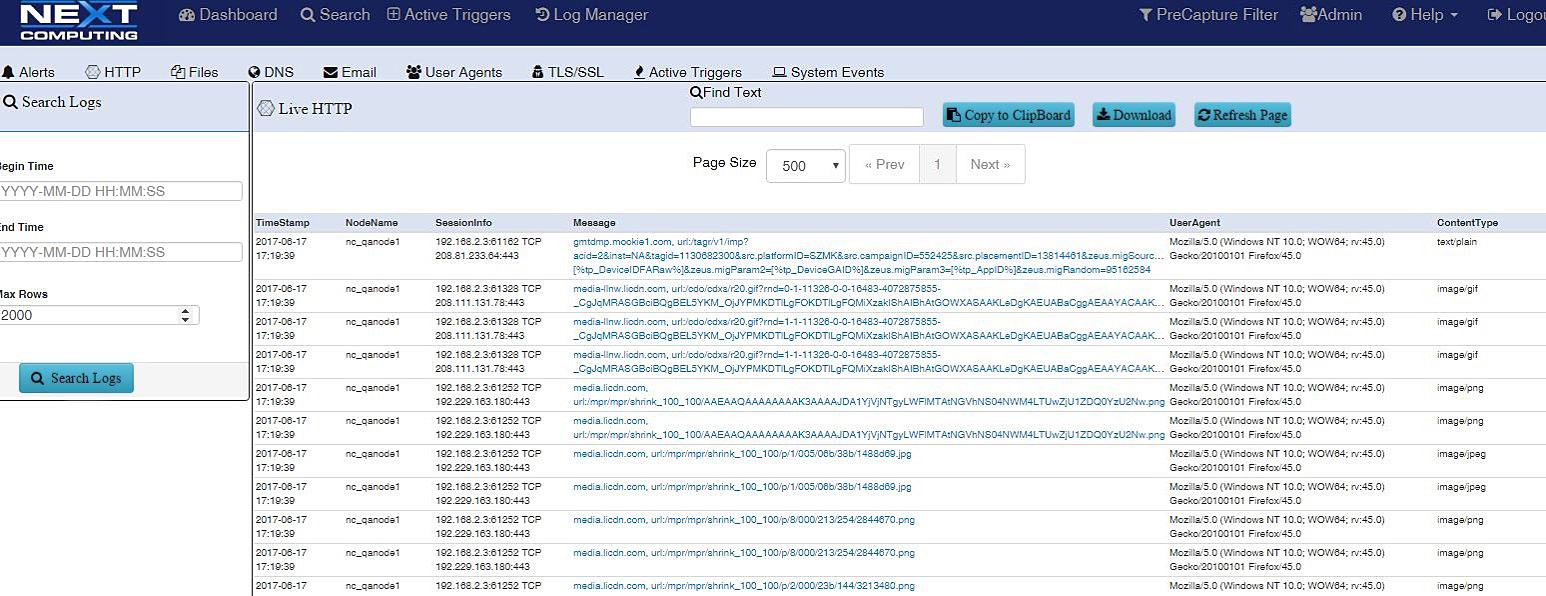
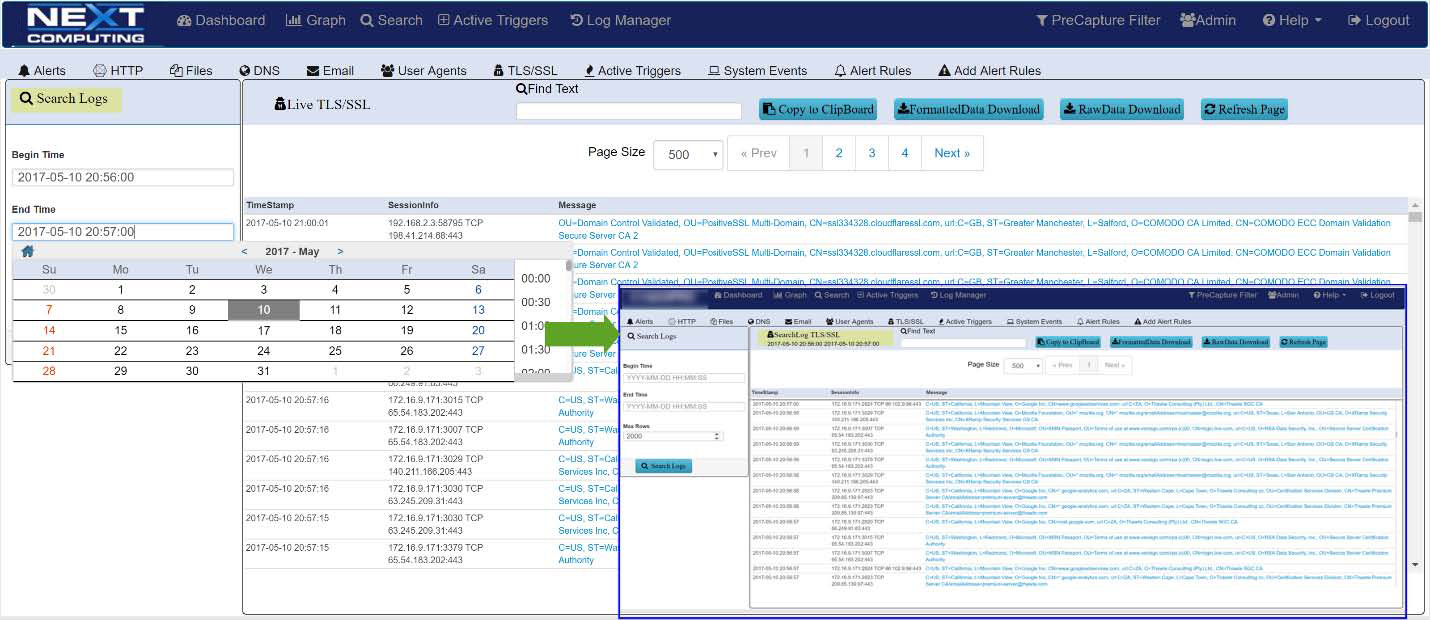
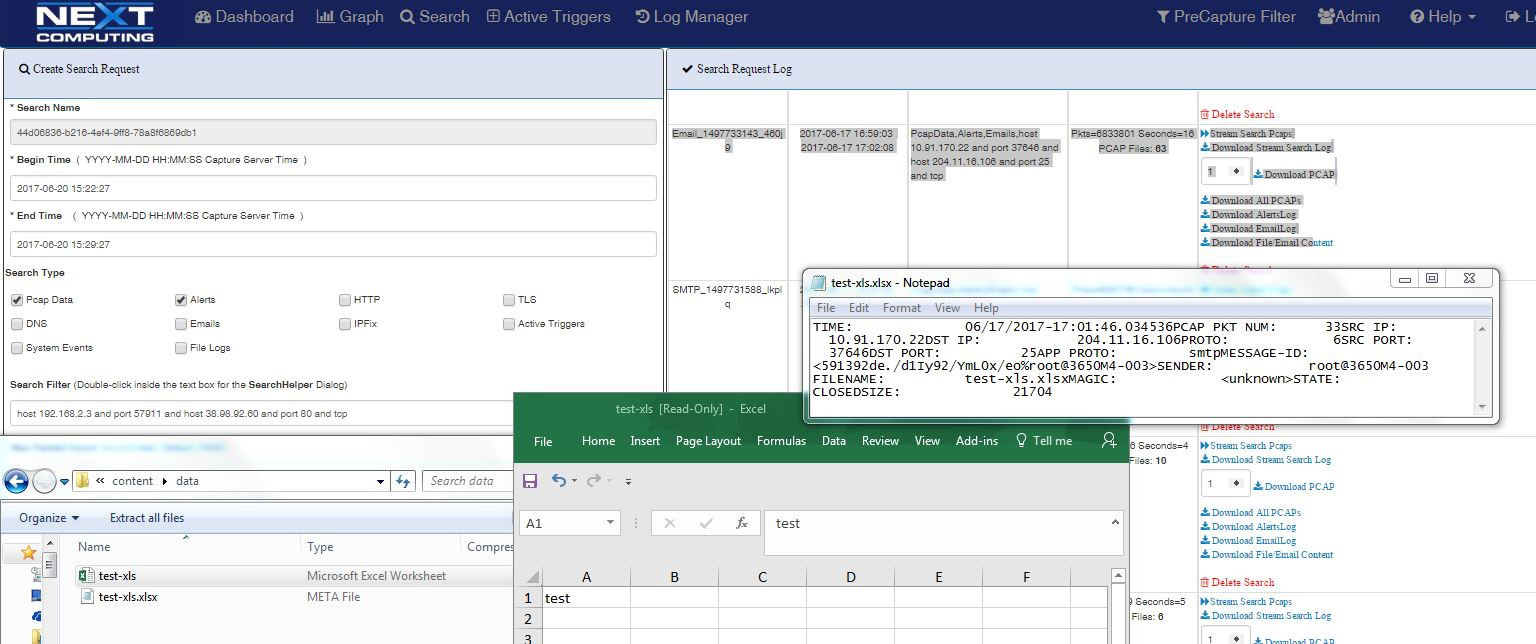
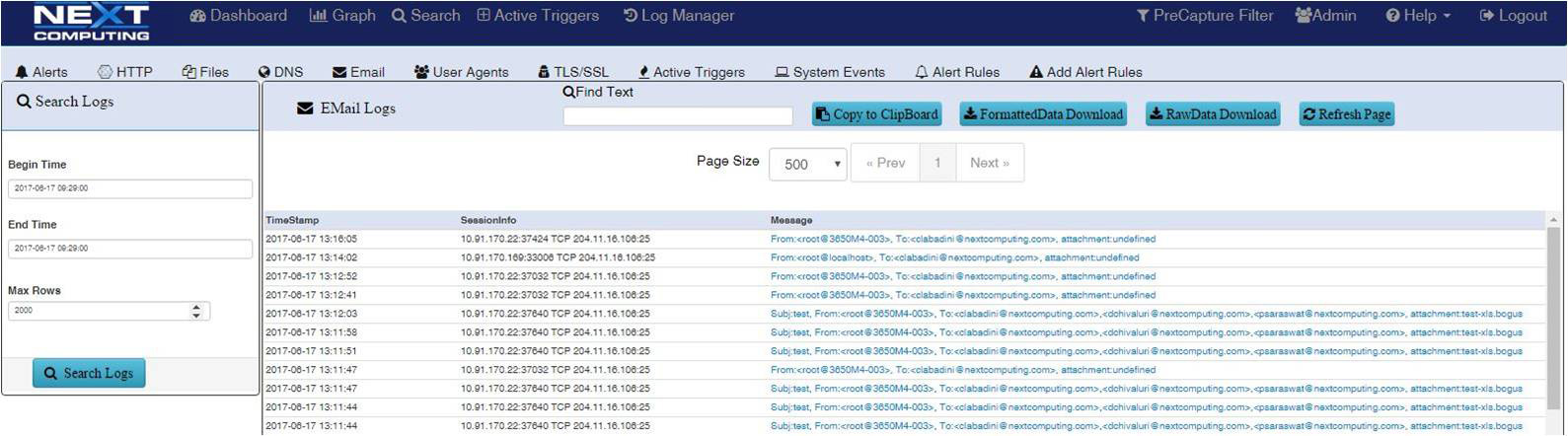
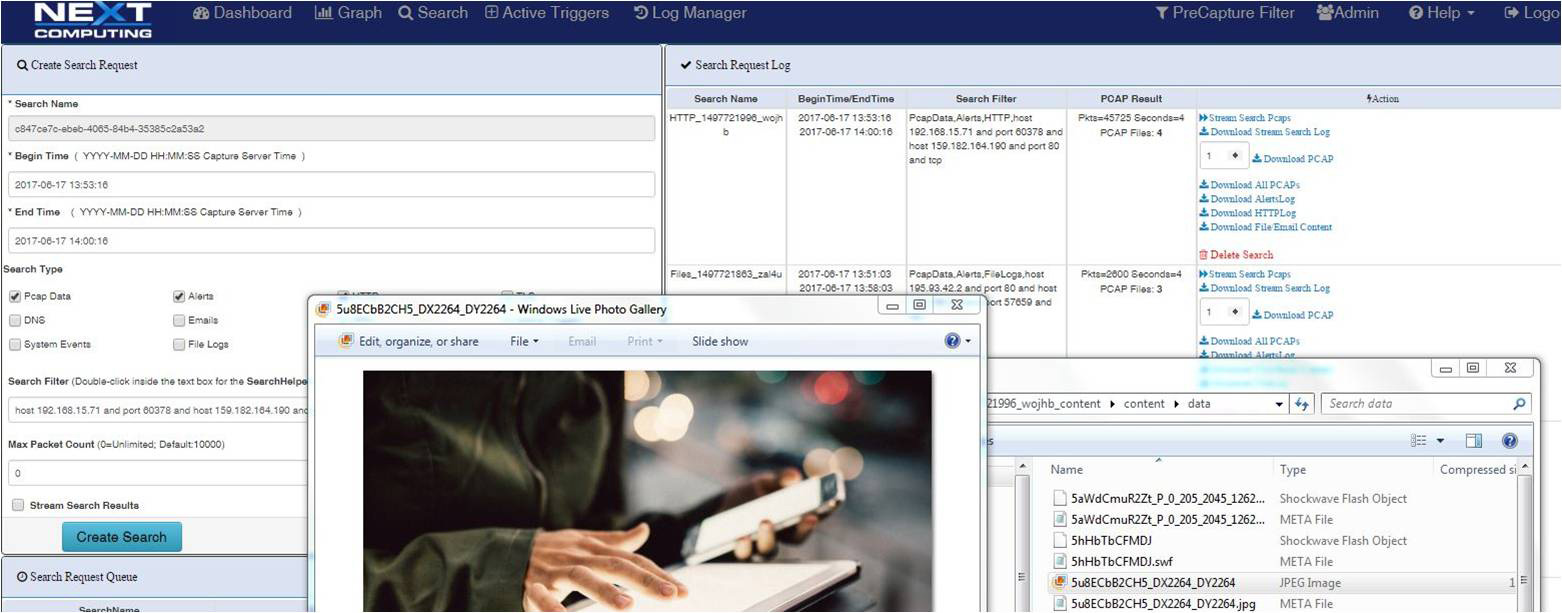
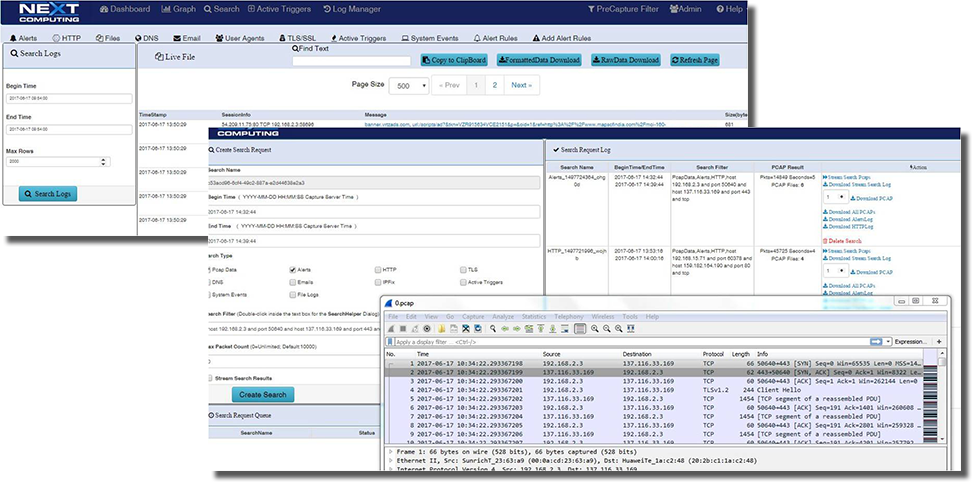
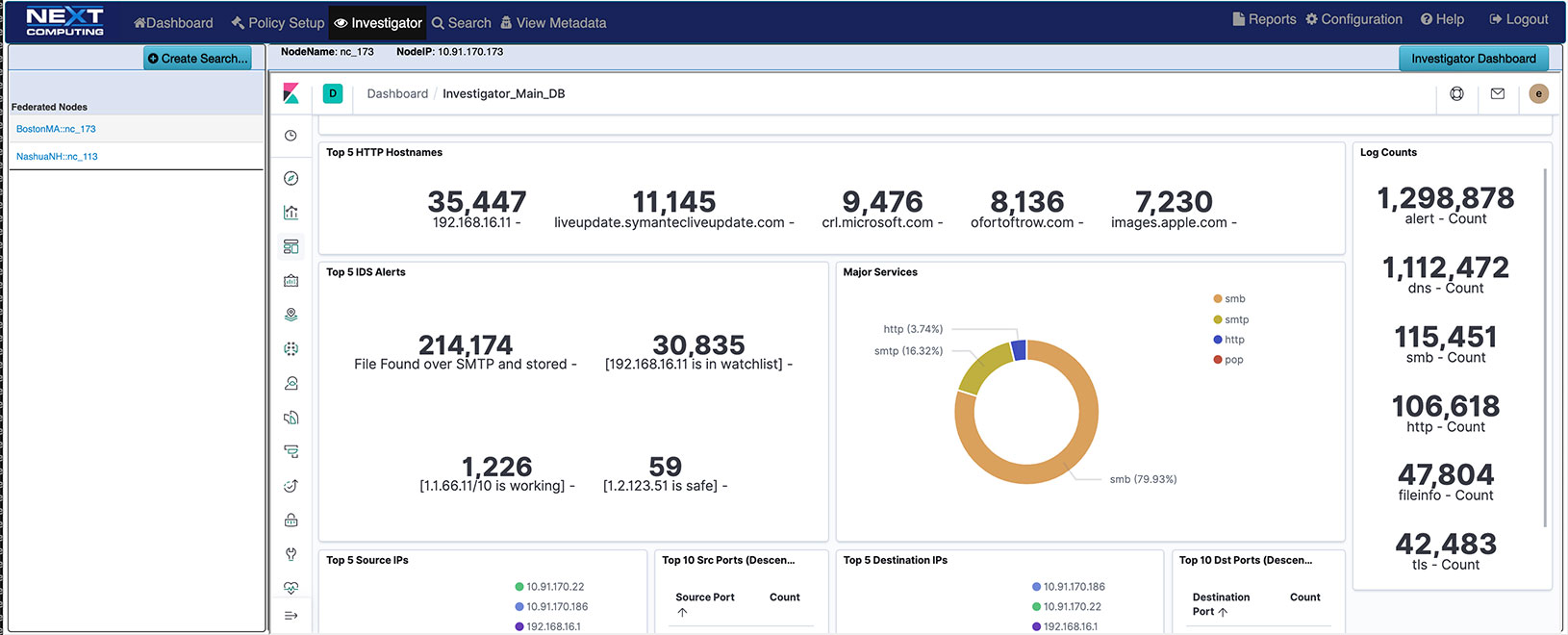
LOG INVESTIGATOR – EVENT SEARCH ACTIONS
- One-click time-based search
- Text-based search of alerts
- All IoC events correlated with PCAPs, NetFlow records, and sessionized logs